Smarter machine-learning models can improve phishing website detection
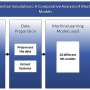
Phishing websites remain a persistent cybersecurity threat, exploiting users by imitating trusted online services. New machine-learning tools could help organizations flag more phishing sites before they harm users and steal credentials. A Sultan Qaboos University […]