-
 Biometric IDs are being rolled out in Africa. Study reveals the risks and pitfallsAcross Africa, governments are introducing digital systems that use individuals' unique physical measurements to identify them. These systems collect citizens' biometric and personal data and use it to give people access to essential public services like voting, health care, education and social protection. Biometric digital identification systems are often promoted... Read more
Biometric IDs are being rolled out in Africa. Study reveals the risks and pitfallsAcross Africa, governments are introducing digital systems that use individuals' unique physical measurements to identify them. These systems collect citizens' biometric and personal data and use it to give people access to essential public services like voting, health care, education and social protection. Biometric digital identification systems are often promoted... Read more -
 Your car's tire sensors could be used to track youResearchers at IMDEA Networks Institute, together with European partners, have found that tire pressure sensors in modern cars can unintentionally expose drivers to tracking. Over a ten-week study, they collected signals from more than 20,000 vehicles, revealing a hidden privacy risk and highlighting the need for stronger security measures in... Read more
Your car's tire sensors could be used to track youResearchers at IMDEA Networks Institute, together with European partners, have found that tire pressure sensors in modern cars can unintentionally expose drivers to tracking. Over a ten-week study, they collected signals from more than 20,000 vehicles, revealing a hidden privacy risk and highlighting the need for stronger security measures in... Read more -
 Ensuring smartphones have not been tampered withWith increasing cyberattacks and government data breaches, one of the most important devices to keep secure is the one in everyone's pocket: smartphones. The problem is that it is difficult to check that a smartphone has not been tampered with without the risk of unintentionally damaging the device itself.... Read more
Ensuring smartphones have not been tampered withWith increasing cyberattacks and government data breaches, one of the most important devices to keep secure is the one in everyone's pocket: smartphones. The problem is that it is difficult to check that a smartphone has not been tampered with without the risk of unintentionally damaging the device itself.... Read more -
 AI 'blind spot' could allow attackers to hijack self-driving vehiclesA newly discovered vulnerability could allow cybercriminals to silently hijack the artificial intelligence (AI) systems in self-driving cars, raising concerns about the security of autonomous systems increasingly used on public roads. Georgia Tech cybersecurity researchers discovered the vulnerability, dubbed VillainNet, and found it can remain dormant in a self-driving vehicle's... Read more
AI 'blind spot' could allow attackers to hijack self-driving vehiclesA newly discovered vulnerability could allow cybercriminals to silently hijack the artificial intelligence (AI) systems in self-driving cars, raising concerns about the security of autonomous systems increasingly used on public roads. Georgia Tech cybersecurity researchers discovered the vulnerability, dubbed VillainNet, and found it can remain dormant in a self-driving vehicle's... Read more -
 Mississippi hospital system closes all clinics after ransomware attackA ransomware attack forced the University of Mississippi Medical Center to close clinics and cancel elective procedures for a second day on Friday.... Read more
Mississippi hospital system closes all clinics after ransomware attackA ransomware attack forced the University of Mississippi Medical Center to close clinics and cancel elective procedures for a second day on Friday.... Read more -
 Cyber-attacks could disrupt smart factories by targeting time itselfA cyber-attack does not always need to steal data or shut systems down to cause damage. Sometimes it only needs to shift the clock. Researchers at the University of East London (UEL), in collaboration with industry, have identified a critical weakness in the timing systems that keep modern automated industries... Read more
Cyber-attacks could disrupt smart factories by targeting time itselfA cyber-attack does not always need to steal data or shut systems down to cause damage. Sometimes it only needs to shift the clock. Researchers at the University of East London (UEL), in collaboration with industry, have identified a critical weakness in the timing systems that keep modern automated industries... Read more -
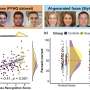 People are overconfident about spotting AI faces, study findsMost people believe they can spot AI-generated faces, but that confidence is out of date, research from UNSW Sydney and the Australian National University (ANU) has demonstrated. With AI-generated faces now almost impossible to distinguish from real ones, this misplaced confidence could make individuals and organizations more vulnerable to scammers,... Read more
People are overconfident about spotting AI faces, study findsMost people believe they can spot AI-generated faces, but that confidence is out of date, research from UNSW Sydney and the Australian National University (ANU) has demonstrated. With AI-generated faces now almost impossible to distinguish from real ones, this misplaced confidence could make individuals and organizations more vulnerable to scammers,... Read more -
 Spanish police arrest hacker who booked luxury hotels for one centSpanish police said Wednesday they had arrested a 20-year-old man who allegedly hacked a hotel booking website to reserve luxury rooms for as little as one cent, in the first known cybercrime of its kind.... Read more
Spanish police arrest hacker who booked luxury hotels for one centSpanish police said Wednesday they had arrested a 20-year-old man who allegedly hacked a hotel booking website to reserve luxury rooms for as little as one cent, in the first known cybercrime of its kind.... Read more -
 Amazon's Ring wanted to track your pets. It revealed the future of surveillanceAs a career counterintelligence officer for the US Federal Bureau of Investigation (FBI) and Defense Intelligence Agency, I worked inside a fully integrated intelligence system. Signals intelligence from the National Security Agency guided investigations. Satellite imagery from the National Reconnaissance Office provided visibility into hostile environments. Human intelligence came through... Read more
Amazon's Ring wanted to track your pets. It revealed the future of surveillanceAs a career counterintelligence officer for the US Federal Bureau of Investigation (FBI) and Defense Intelligence Agency, I worked inside a fully integrated intelligence system. Signals intelligence from the National Security Agency guided investigations. Satellite imagery from the National Reconnaissance Office provided visibility into hostile environments. Human intelligence came through... Read more -
 Advanced security technology is rarely used—research offers a solutionModern and powerful security technology that protects against hacking attempts is used to a very limited extent—despite having been available to developers for more than a decade. Researchers at Umeå University can now reveal why the technology fails to take hold. "At the same time, we present an automated solution... Read more
Advanced security technology is rarely used—research offers a solutionModern and powerful security technology that protects against hacking attempts is used to a very limited extent—despite having been available to developers for more than a decade. Researchers at Umeå University can now reveal why the technology fails to take hold. "At the same time, we present an automated solution... Read more -
 Why 'zero-knowledge encryption' may not stop password theft if servers are hackedPeople who regularly use online services have between 100 and 200 passwords. Very few can remember every single one. Password managers are therefore extremely helpful, allowing users to access all their passwords with just a single master password.... Read more
Why 'zero-knowledge encryption' may not stop password theft if servers are hackedPeople who regularly use online services have between 100 and 200 passwords. Very few can remember every single one. Password managers are therefore extremely helpful, allowing users to access all their passwords with just a single master password.... Read more -
 Interpol backroom warriors fight cyber criminals 'weaponising' AIFrom perfectly spelled phishing emails to fake videos of government officials, artificial intelligence is changing the game for Interpol's cat-and-mouse fight against cybercrime at its high-tech war rooms in Singapore.... Read more
Interpol backroom warriors fight cyber criminals 'weaponising' AIFrom perfectly spelled phishing emails to fake videos of government officials, artificial intelligence is changing the game for Interpol's cat-and-mouse fight against cybercrime at its high-tech war rooms in Singapore.... Read more -
 Cybersecurity spending may pay off: Study links readiness to stronger returnsThe infamous Target data breach during the 2013 holiday shopping season, which cost the company more than $200 million in damages, has since been hailed as a landmark case in cybersecurity. Exposure to these threats has only increased as businesses continue to expand their digital footprints. That's why, as a... Read more
Cybersecurity spending may pay off: Study links readiness to stronger returnsThe infamous Target data breach during the 2013 holiday shopping season, which cost the company more than $200 million in damages, has since been hailed as a landmark case in cybersecurity. Exposure to these threats has only increased as businesses continue to expand their digital footprints. That's why, as a... Read more -
 Research shows companies can gain advantage by prioritizing customer privacyFor many companies, customer privacy is often seen as a regulatory burden that limits data use and personalization rather than as a business opportunity. Research by Natalie Chisam at the University of Nebraska–Lincoln reveals companies that handle customer data with transparency, care, and clear communication can gain a measurable competitive... Read more
Research shows companies can gain advantage by prioritizing customer privacyFor many companies, customer privacy is often seen as a regulatory burden that limits data use and personalization rather than as a business opportunity. Research by Natalie Chisam at the University of Nebraska–Lincoln reveals companies that handle customer data with transparency, care, and clear communication can gain a measurable competitive... Read more -
 Your AI chat may reveal more than you thinkAs the use of large language model agents, such as virtual assistants or chatbots, increases at work, at home and in schools, users may be sharing more private information than they realize, according to new research from the University at Buffalo School of Management.... Read more
Your AI chat may reveal more than you thinkAs the use of large language model agents, such as virtual assistants or chatbots, increases at work, at home and in schools, users may be sharing more private information than they realize, according to new research from the University at Buffalo School of Management.... Read more
© 2024 E-RADIO.CA - CANADA'S LATEST TECH NEWS HEADLINES, STORIES AND MORE.
